The role of security in software development has grown much more significant with the changing patterns of the latest cyber trends. Given the current threat landscape, developers are increasingly prioritising languages that come equipped with built-in security features, robust frameworks, and community support for good sanitation practices. In this blog, we will discuss what security stands for in the world of programming languages and what parameters are used to measure it, along with our recommendations for the most secure languages of 2025.
Understanding Security in Programming Languages
Not all languages are created equal in terms of security. Many place extra security requirements on developers who are already under pressure. Programming languages like C and C++ offer greater control over system resources but require developers to handle potential security risks manually. Because programming components like memory, threads, and variable types can be changed in any way, languages are extremely powerful but also vulnerable to cyberattacks. As a result, when developing applications, it’s crucial to adhere to secure development methods and conduct vulnerability assessments to make sure the project is going in the right direction.
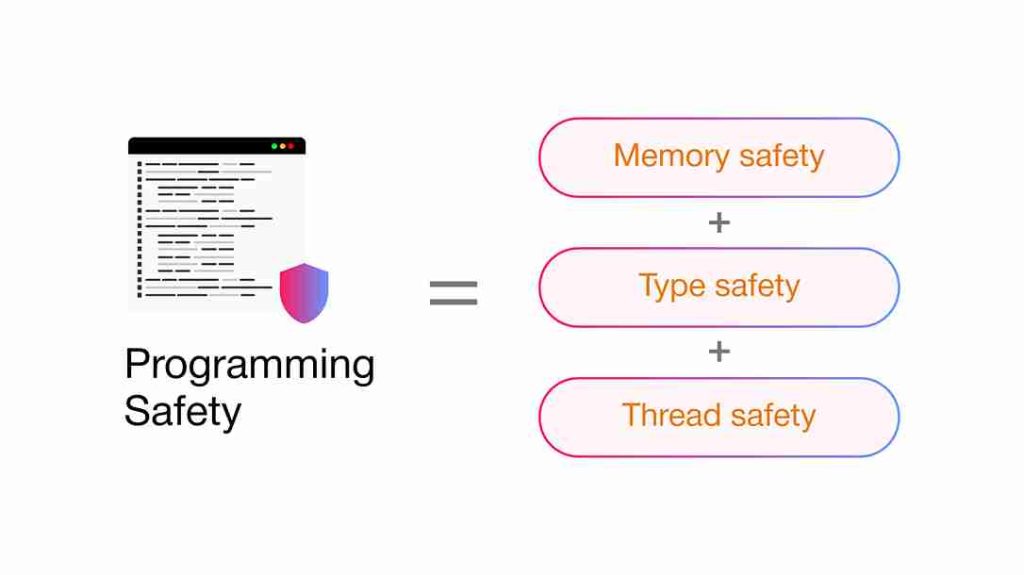
Selecting a programming language is not a matter of sheer wish but rather a discussion based on calculations, similar to choosing a cybersecurity company. If the language is not safe, it might lead to vulnerabilities that will eventually invite an attack on your systems. This is why programming language selection can have a big impact. However, the conundrum lies in the fact that no programming language is safe, even though safe languages are thought to be more secure than unsafe ones. So what do you do? Well, you look for security features that are suitable to your requirements and then select the programming language. Here is a list of a few additional security features that safe programming languages must have:
- Memory safety
- Smooth error handling
- Type safety
- Supports pure functions
- Thread safety
- Enforces abstractions
- Precise & well-defined semantics
Although no language can completely protect a system from attacks, some languages serve as a great first wall of fortification by including built-in defences against typical weaknesses at compile time. A thorough grasp of the languages, their built-in security features, and their potential can help you safeguard your company’s software supply chain. In the next section of this blog, we list the top 10 programming languages for 2025.
10 Most Secure Programming Languages in 2025
Given that there are more than 700 programming languages available, you probably want to determine which one is best. In the end, your decision will be influenced by your professional objectives, skill level, and the languages that are optimal for your company in their workplaces. Here are the 10 most secure programming languages for 2025 as ranked for design, widespread adoption in secure environments, and past record of vulnerability reduction.
Rust
Based on current trends, in 2025, Rust has hardened its position as the top of the line for secure programming languages. Rust aims for predictable and secure concurrent programs, and as a result, they reduce some common runtime vulnerabilities, such as buffer overflows and null pointer dereferences, that exist on a spectrum of performance. Based on its ownership system, it guarantees secure memory management, the most critical part of a system, especially for operating systems, web browsers, and blockchain applications.
Key Features:
- Memory safety ownership model
- Strong static type system
- Eliminates garbage collector, hence eliminating runtime vulnerabilities.
Python
The good news is that Python continues to be a safe bet, and it’s only getting safer with the growing number of libraries and frameworks built specifically for secure app development. This language keeps on updating itself and continues to fix security bugs and give developers best practices via Bandit and PyLint.
Key Features:
- Lots of libraries for doing secure things with data, e.g., cryptography.
- Fast vulnerability resolution by an active community
- Django with built-in security features
Java
Java’s ‘Write once, run anywhere’ philosophy has made it an application of choice for enterprise-level applications. Part of this robust security model consists of features such as bytecode verification, sandboxing, and secure class loading that make it very secure for applications on the web and in the backend.
Key Features:
- Automatic memory management and garbage collection
- e.g. (JVM) security manager
- Updates with regular addressing of vulnerabilities
Go (Golang)
A key attraction of Go is its simplicity and lean standard library, avoiding the need for dozens of third-party libraries that might themselves be sources of vulnerabilities. Built-in tools for managing concurrency and errors provide secure and scalable software development.
Key Features:
- Memory safety built-in garbage collection
- Prevention of errors by catching them at compile time
- Preventing race conditions using a CSP-based concurrency model
Swift
Apple prefers Swift when it comes to building apps for iOS and macOS, mainly due to its modern safety features that protect your software against common security problems. Mobile application development, with its memory safety, strict typing, and automatic reference counting (ARC), are all safer options.
Key Features:
- Automatic memory management
- Reduce runtime errors by strong static typing.
- Modern syntax and features that also enhance safety.
Kotlin
Android has now finally come a great way to do secure development with Kotlin, even better against ProGuard. The concise syntax of this language reduces the chances of any mistakes made by humans, and its null safety feature disables null pointer exceptions, a big vulnerability in Java. Kotlin is incredibly compatible with a range of other languages, like Java, and serves excellently as a secure language for mobile and backend applications.
Key Features:
- To prevent crashes, it comes equipped with null safety.
- Baked-in security coding practices in the language.
- Cloud-based workflows for multiple platforms
Haskell
Although Haskell is not as mainstream, it has quite a good reputation for a strong emphasis on immutability and type safety. A functional programming paradigm minimises side effects, leading to inherently more secure applications for certain types of applications.
Key Features:
- A pure functional programming model
- Prevents common bugs with the strong type system
- Appropriate for academic as well as security-critical applications.
TypeScript
With TypeScript being a superset of JavaScript, it is a much more secure tool for modern web development. This language helps developers find errors during the compile time, so it leads to reducing the runtime vulnerability for large-scale applications.
Key Features:
- Enhanced safety of static typing
- Integration with JavaScript
- Secure web development frameworks like Angular support.
C#
Secure application development for Windows and Azure platforms continues to be dominated by C#. It’s a framework built on top of the .NET framework and is inherently type-safe, has garbage collection, and, because it is integrated with the .NET framework, this makes it easy for the developer to create secure and highly performant applications.
Key Features:
- Memory-safe programming practices
- Some examples of secure coding frameworks are those like .NET Core.
- Most advanced debugging and error-handling tools
Ruby
With Ruby on Rails, Ruby, in particular, will always be a safe language to develop a web application. Secure coding practices are made simple by its convention-over-configuration philosophy, and its hypersolid community means that vulnerabilities get patched quickly.
Key Features:
- Rails’ framework-level security features
- Decreases developer errors in simplified syntax
- Secure coding support
Looking Forward: Security Needs to be a Development Priority
Building secure software isn’t just about choosing a secure programming language. These languages provide functionality to lower the risks, but in the end, security boils down to how developers use them. The first steps towards protecting applications are to start embracing secure coding practices, running regular code reviews for vulnerabilities, and making sure applications are patched regularly.
In conclusion, the quality of a secure programming language’s standard library, the lucidity of its documentation, and the predictability of its functions are its true strengths, even though memory safety and typing are crucial. Developers can avoid typical security problems and create more secure web applications by concentrating on these areas. Don’t recreate the wheel when it comes to security; instead, make use of the resources and tools that the language and framework offer. Despite the evolution of the secure programming landscape in 2025, these languages are likely to expand further as tools to build otherwise robust and secure applications within a growing technology-dependent world.

















 TRAVEL & HOSPITALITY
TRAVEL & HOSPITALITY HEALTHCARE
HEALTHCARE RETAILS & ECOMMERCE
RETAILS & ECOMMERCE BANKING & FINANCIAL
BANKING & FINANCIAL AutoMobile
AutoMobile MANUFACTURING
MANUFACTURING FOOD
FOOD EDUCATION
EDUCATION